ORUTA: PRIVACY-PRESERVING PUBLIC
AUDITING
FOR SHARED DATA IN THE CLOUD
TO VIEW THE OUTPUT CLICK HERE
TO VIEW THE OUTPUT CLICK HERE
ABSTRACT:
With
cloud storage services, it is commonplace for data to be not only stored in the
cloud, but also shared across multiple users. However, public auditing for such
shared data — while preserving identity privacy — remains to be an open
challenge. In this paper, we propose the first privacy-preserving mechanism
that allows public auditing on shared data stored in the cloud. In particular, we
exploit ring signatures to compute the verification information needed to audit
the integrity of shared data. With our mechanism, the identity of the signer on
each block in shared data is kept private from a third party auditor (TPA), who
is still able to publicly verify the integrity of shared data without
retrieving the entire file. Our experimental results demonstrate the
effectiveness and efficiency of our Proposed
mechanism when auditing shared data.
EXISTING SYSTEM:
We
believe that sharing data among multiple users is perhaps one of the most
engaging features that motivates cloud storage. A unique problem introduced
during the process of public auditing for shared data in the
cloud is how to preserve identity privacy from the TPA, because the identities
of signers on shared data may indicate that a particular user in the group or a
special block in shared data is a higher valuable target than others.
DISADVANTAGES OF
EXISTING SYSTEM:
- After performing several auditing tasks, some private and sensitive information may reveal to the TPA.
- On one hand, most of the blocks in shared file are signed by A, which may indicate that A is a important role in this group, such as a group leader.
- On the other hand, the one block is frequently modified by different users.
PROPOSED SYSTEM:
We
propose ORUTA (One Ring to Rule Them All), a new privacy preserving public
auditing mechanism for shared data in an untrusted cloud. In ORUTA, we utilize
ring signatures to construct homomorphic authenticators, so that the third
party auditor is able to verify the integrity of shared data for a group of
users without retrieving the entire data — while the identity of the signer on
each block in shared data is kept private from the TPA. In addition, we further
extend our mechanism to support batch auditing, which can audit multiple shared
data simultaneously in a single auditing task. Meanwhile, ORUTA continues to
use random masking to support data privacy during public auditing, and leverage
index hash tables to support fully dynamic operations on shared data.
ADVANTAGES OF PROPOSED
SYSTEM:
- We only consider how to audit the integrity of shared data in the cloud with static groups. It means the group is pre-defined before shared data is created in the cloud and the membership of users in the group is not changed during data sharing.
- The Original user is responsible for deciding who is able to share her data before outsourcing data to the cloud.
- The cloud with dynamic groups — a new user can be added into the group and an existing group member can be revoked during data sharing.
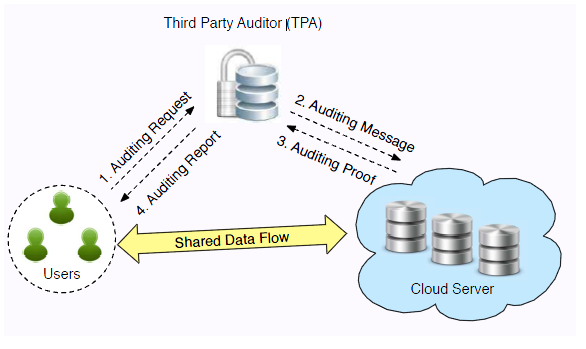
SYSTEM ARCHITECHTURE:
SYSTEM CONFIGURATION:-
HARDWARE REQUIREMENTS:-
ü Processor - Pentium –IV
ü Speed - 1.1 Ghz
ü RAM - 512 MB(min)
ü Hard
Disk - 40 GB
ü Key
Board - Standard Windows Keyboard
ü Mouse - Two or Three Button Mouse
ü Monitor - LCD/LED
SOFTWARE
REQUIREMENTS:
•
Operating system : Windows XP.
•
Coding Language : ASP .Net
•
Data Base : SQL
Server 2005
•
Tool : VISUAL STUDIO 2008.
REFERENCE:
Boyang
Wang, Baochun Li, and Hui Li, “ORUTA:
PRIVACY-PRESERVING PUBLIC AUDITING FOR SHARED DATA IN THE CLOUD” IEEE
TRANSACTIONS ON Cloud Computing, VOL 1,ISS 2, FEBRAURY 2013
No comments:
Post a Comment