Abstract
Development of
authorization mechanisms for secure information access by a large community of
users in an open environment is an important problem in the ever-growing
Internet world. In this paper we propose a computational dynamic trust model
for user authorization, rooted in findings from social science. Unlike most
existing computational trust models, this model distinguishes trusting belief
in integrity from that in competence in different contexts and accounts for
subjectivity in the evaluation of a particular trustee by different trusters.
Simulation studies were conducted to compare the performance of the proposed
integrity belief model with other trust models from the literature for
different user behavior patterns. Experiments show that the proposed model
achieves higher performance than other models especially in predicting the
behavior of unstable users.
Aim
The main aim is
to compute dynamic trust model for user authorization to secure
information access by a large community of users in an open environment in the ever-growing Internet world.
Scope:
The scope is to enable automated trust
management that mimics trusting behaviors, trusting belief in integrity from
that in competence
Existing
System
Social trust model defines five
conceptual trust types:
1) trusting behavior,
2) trusting intention,
3) trusting belief,
4) institution-based trust,
5) disposition to trust.
Trusting behavior is an action that
increases a truster's risk or makes the truster vulnerable to the trustee.
Trusting
intention indicates that a truster is willing to engage in
trusting behaviors with the trustee.
Trusting
belief is a truster's subjective belief in the fact that a
trustee has attributes beneficial to the truster. The following are the four
attributes used most often: Competence, Benevolence, Integrity, Predictability
Institution-based
trust is the belief that proper structural conditions are
in place to enhance the probability of achieving a successful outcome.
Two subtypes of institution- based trust
are:
1. Structural assurance 2.
Situational normality.
Disposition to trust characterizes
a truster's general propensity to depend on others across a broad spectrum of
situations. Two subtypes of disposition to trust are: 1. Faith in human 2.
Trusting stance
Trust intention and trusting belief are
situation and trustee specific. Institution-based trust is situation specific.
Disposition to trust is independent of situation and trustee. Trusting belief
positively relates to trusting intention, which in turn results in the trusting
behavior. Institution- based trust positively affects trusting belief and
trusting intention. Structural assurance is more related to trusting intention
while situational normality affects both. Disposition to trust positively
influences institution-based trust, trusting belief and trusting intention.
Faith in humanity impacts trusting belief. Trusting stance influences trusting
intention.
The existing approaches are to extract
reputation from the social network topology that encodes reputation
information, for social networks, based on the concept of
feedback centrality, for access control in P2P networks,
based on the assumption of transitivity of trust in social networks, where a
simple mathematical model based on fuzzy set membership is used to calculate
the trustworthiness of each node in a trust graph symbolizing interactions
between network nodes, for nodes in a P2P network, based on the history of
interactions between nodes.
Disadvantages
Although the existing approaches integrate context
into trust computation, their application is limited to specific domains.
Proposed
System
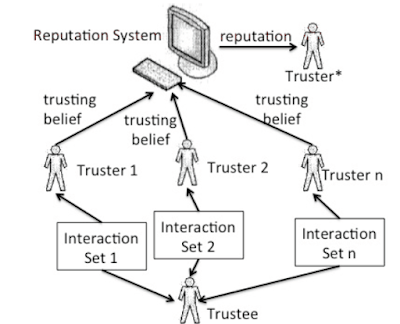
In this paper we
propose a computational dynamic trust model for user authorization, rooted in
findings from social science. This model distinguishes trusting belief in
integrity from that in competence in different contexts and accounts for
subjectivity in the evaluation of a particular trustee by different trusters. The
proposed model accounts for different types of trust. Specifically, it
distinguishes trusting belief in integrity from that in competence. The model
takes into account the subjectivity of trust ratings by different entities, and
introduces a mechanism to eliminate the impact of subjectivity in reputation
aggregation.
Advantages
The model evaluates trust separately for
each property of each component of a platform.The proposed dynamic trust model enables
automated trust management that mimics trusting behaviors in society, such as
selecting a corporate partner, forming a coalition, or choosing negotiation
protocols or strategies in e-commerce. The formalization of trust helps in
designing algorithms to choose reliable resources in peer-to-peer systems,
developing secure protocols for ad hoc networks and detecting deceptive agents
in a virtual community. Experiments in a simulated trust environment show that
the proposed integrity trust model performs better than other major trust
models in predicting the behavior of users whose actions change based on
certain patterns over time.
System
Architecture
SYSTEM CONFIGURATION
HARDWARE REQUIREMENTS:-
· Processor - Pentium –III
·
Speed - 1.1 Ghz
·
RAM - 256 MB(min)
·
Hard
Disk - 20 GB
·
Floppy
Drive - 1.44 MB
·
Key
Board - Standard Windows Keyboard
·
Mouse - Two or Three Button Mouse
·
Monitor -
SVGA
SOFTWARE REQUIREMENTS:-
·
Operating
System : Windows 7
·
Front
End : JSP AND SERVLET
·
Database
: MYSQL
·
Tool :NETBEANS
References
Bhargava, B, Yi Lu, Angin, P. “A
COMPUTATIONAL DYNAMIC TRUST MODEL FOR USER AUTHORIZATION” Dependable and Secure
Computing, IEEE Transactions on
(Volume:12 , Issue: 1 ) February
2014.
No comments:
Post a Comment