Abstract
In
the cloud, for achieving access control and keeping data confidential, the data
owners could adopt attribute-based encryption to encrypt the stored data. Users
with limited computing power are however more likely to delegate the mask of
the decryption task to the cloud servers to reduce the computing cost. As a
result, attribute-based encryption with delegation emerges. Still, there are
caveats and questions remaining in the previous relevant works. For instance,
during the delegation, the cloud servers could tamper or replace the delegated
cipher text and respond a forged computing result with malicious intent. They
may also cheat the eligible users by responding them that they are ineligible
for the purpose of cost saving. Furthermore, during the encryption, the access
policies may not be flexible enough as well. Since policy for general circuits
enables to achieve the strongest form of access control, a construction for
realizing circuit cipher text-policy attribute-based hybrid encryption with
verifiable delegation has been considered in our work. In such a system,
combined with verifiable computation and encrypt-then-Mac mechanism, the data
confidentiality, the fine-grained access control and the correctness of the
delegated computing results are well guaranteed at the same time. Besides, our
scheme achieves security against chosen-plaintext attacks under the k-multi linear
Decisional Diffie-Hellman assumption. Moreover, an extensive simulation
campaign confirms the feasibility and efficiency of the proposed solution.
Aim
The
main aim is to provide an efficient method to share and protect the
confidential information between users with limited power and data owners with
vast amount of data in the cloud.
Scope
The
scope is to provide policy for general circuits enables to achieve the
strongest form of access control, a construction for realizing circuit cipher
text-policy attribute-based hybrid encryption with verifiable delegation has
been considered.
Existing System
Attribute-based
encryption
proposed
the notion of attribute-based encryption (ABE).
They
focused on policies across multiple authorities and the issue of what
expressions they could achieve. Up until recently, raised a construction for
realizing KPABE for general circuits. Prior to this method, the strongest form
of expression is boolean formulas in ABE systems, which is still a far cry from
being able to express access control in the form of any program or circuit.
Actually, there still remain two problems. The first one is their have no
construction for realizing CPABE for general circuits, which is conceptually
closer to traditional access control. The other is related to the efficiency,
since the exiting circuit ABE scheme is just a bit encryption one. Thus, it is
apparently still remains a pivotal open problem to design an efficient circuit
CP-ABE scheme.
Hybrid
encryption.
Existing
system proposed the generic KEM/DEM construction for hybrid encryption which
can encrypt messages of arbitrary length. Based on their ingenious work, a
one-time MAC were combined with symmetric encryption to develop the KEM/DEM
model for hybrid encryption. Such improved model has the advantage of achieving
higher security requirements. ABE with Verifiable Delegation. Since the
introduction of ABE, there have been advances in multiple directions.The
application of outsourcing computation is one of an important direction. It designed
the first ABE with outsourced decryption
scheme to reduce the computation cost during decryption. However, since the
data owner generates a commitment without any secret value about his identity,
the untrusted server can then forge a commitment for a message he chooses. Thus
the ciphertext relating to the message is at risk of being tampered. Further
more, just modify the commitments for the ciphertext relating to the message is
not enough. The cloud server can deceive the user with proper permissions by
responding the terminator ⊥ to cheat that he/she
is not allowed to access to the data.
Disadvantages
There
are caveats and questions remaining in the previous relevant works. For
instance, during the delegation, the cloud servers could tamper or replace the
delegated cipher text and respond a forged computing result with malicious
intent. They may also cheat the eligible users by responding them that they are
ineligible for the purpose of cost saving. Furthermore, during the encryption,
the access policies may not be flexible enough as well.
Proposed System
This
project proposes a concrete circuit ciphertext-policy attribute-based hybrid
encryption with verifiable delegation scheme based on the multilinear maps and
the verifiable computing technology under cloud environment.
Advantages
· This
project achieves security against chosen-plaintext attacks under the k-multi
linear Decisional Diffie-Hellman assumption. Moreover, an extensive simulation
campaign confirms the feasibility and efficiency of the proposed solution.
· An
extensive simulation campaign confirms the feasibility and efficiency.
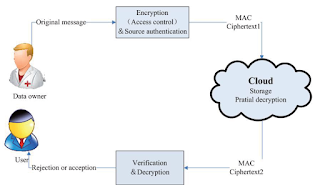
System
Architecture
System Configuration
Hardware Requirements
- Speed - 1.1 Ghz
- Processor - Pentium IV
- RAM - 512 MB (min)
- Hard Disk - 40 GB
- Key Board - Standard Windows Keyboard
- Mouse - Two or Three Button Mouse
- Monitor - LCD/LED
Software
requirements
- Operating System : Windows 7
- Front End : ASP.Net and C#
- Database : MSSQL
- Tool : Microsoft Visual studio
References
Wen,
Q. , Li, W. , Jin, Z., Xu, J. “CIRCUIT CIPHER TEXT-POLICY ATTRIBUTE-BASED
HYBRID ENCRYPTION WITH VERIFIABLE DELEGATION IN CLOUD COMPUTING” Parallel and Distributed Systems, IEEE
Transactions on (Volume:PP , Issue: 99 ) January 2015.
No comments:
Post a Comment