ABSTRACT:
To
protect outsourced data in cloud storage against corruptions, adding fault
tolerance to cloud storage together with data integrity checking and failure
reparation becomes critical. Recently, regenerating codes have gained
popularity due to their lower repair bandwidth while providing fault tolerance.
Existing remote checking methods for regenerating-coded data only provide
private auditing, requiring data owners to always stay online and handle
auditing, as well as repairing, which is sometimes impractical. In this paper,
we propose a public auditing scheme for the regenerating-code-based cloud
storage. To solve the regeneration problem of failed authenticators in the absence
of data owners, we introduce a proxy, which is privileged to regenerate the
authenticators, into the traditional public auditing system model. Moreover, we
design a novel public verifiable authenticator, which is generated by a couple
of keys and can be regenerated using partial keys. Thus, our scheme can
completely release data owners from online burden. In addition, we randomize
the encode coefficients with a pseudorandom function to preserve data privacy.
Extensive security analysis shows that our scheme is provable secure under
random oracle model and experimental evaluation indicates that our scheme is
highly efficient and can be feasibly integrated into the regenerating code-
based cloud storage.
AIM
To
protect outsourced data in cloud storage against corruptions, adding fault
tolerance to cloud storage together with data integrity checking and failure
reparation becomes critical.
SCOPE
We focus on the integrity verification problem in
regenerating-code-based cloud storage, especially with the functional repair
strategy.
EXISTING
SYSTEM
Many
mechanisms dealing with the integrity of outsourced data without a local copy
have been proposed under different system and security models up to now. The
most significant work among these studies are the PDP (provable data
possession) model and POR (proof of retrievability) model, which were
originally proposed for the single-server scenario respectively. Considering
that files are usually striped and
redundantly stored across multi-servers or multi-clouds, explore integrity
verification schemes suitable for such multi-servers or multi clouds setting
with different redundancy schemes, such as replication, erasure codes, and,
more recently, regenerating codes.
DISADVANTAGES:
- To hide data loss or corruption and claiming that the files are still correctly stored in the cloud for reputation or monetary reasons.
- To implement an efficient protocol to perform periodical verifications of their outsourced data to ensure that the cloud indeed maintains their data correctly.
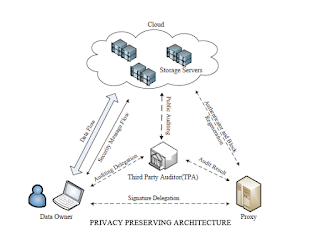
PROPOSED SYSTEM
In
this paper, we propose a public auditing scheme for the regenerating-code-based
cloud storage system, where the data owners are privileged to delegate TPA for
their data validity checking. To protect the original data privacy against the
TPA, we randomize the coefficients in the beginning rather than applying the
blind technique during the auditing process. Considering that the data owner
cannot always stay online in practice, in order to keep the storage available
and verifiable after a malicious corruption, we introduce a semi-trusted proxy
into the system model and provide a privilege for the proxy to handle the
reparation of the coded blocks and authenticators. To better appropriate for
the regenerating-code-scenario, we design our authenticator based on the BLS
signature. This authenticator can be efficiently generated by the data owner
simultaneously with the encoding procedure. Extensive analysis shows that our
scheme is provable secure, and the performance evaluation shows that our scheme
is highly efficient and can be feasibly integrated into a
regenerating-code-based cloud storage system.
ADVANTAGES
- The large size of the outsourced data and the user’s constrained resource capability, the tasks of auditing and reparation in the cloud can be formidable and expensive for the users
- The overhead of using cloud storage should be minimized as much as possible such that a user does not need to perform too many operations to their outsourced data (in additional to retrieving it)
SYSTEM ARCHITECTURE
SYSTEM
CONFIGURATION:-
HARDWARE REQUIREMENTS:-
· Processor - Pentium –III
· Speed - 1.1 Ghz
· RAM - 256 MB(min)
· Hard Disk - 20 GB
· Floppy Drive - 1.44 MB
· Key Board - Standard
Windows Keyboard
· Mouse - Two or Three Button Mouse
· Monitor - SVGA
SOFTWARE REQUIREMENTS:-
·
Operating
System : Windows 7
·
Front
End : JSP AND SERVLET
·
Database : MYSQL
REFERENCE:
Hong
Rong ; Huimei Wang Jian Liu Kun Huang “PRIVACY-PRESERVING
PUBLIC AUDITING FOR REGENERATING-CODE-BASED CLOUD STORAGE” IEEE
Transactions on Information Forensics and Security, VOL 10, ISS 7,MARCH 2015.
No comments:
Post a Comment